Check Who Has Access to Your iPhone and Apple Account
Apple offers several ways to enhance the security and privacy of your iDevice. At any time you sense a threat, you can run a security check to nab the culprit. To be more precise, it’s all about spotting the usual suspects like malicious profiles, custom apps, and making sure that the additional layers of safeguards are enabled. With that said, let’s get started!
View What Devices are Associated with Your Apple ID on iPhone, iPad, and Mac
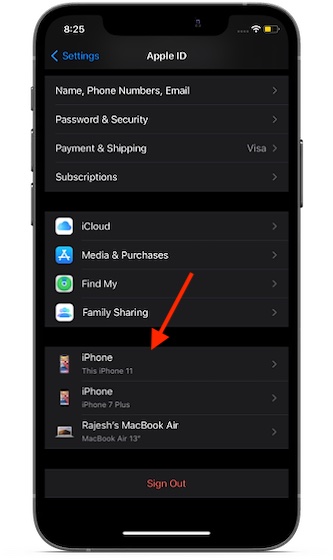
The very first thing that we are going to do is to check what devices are associated with the Apple ID. By linking a device to the iCloud account, anyone can have access to the synced data. Therefore, make sure there is no device synced with your iCloud account. Launch the Settings app on your iPhone or iPad -> your profile/avatar. Now, scroll down below Family Sharing.
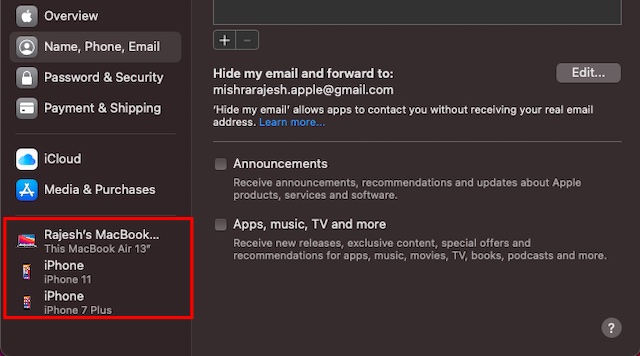
Launch System Preferences on your Mac. (Alternately, click on the Apple menu at the top left corner of the screen and choose System Preferences.) Click on Apple ID. On the next screen, you should see the list of all the linked devices in the sidebar.
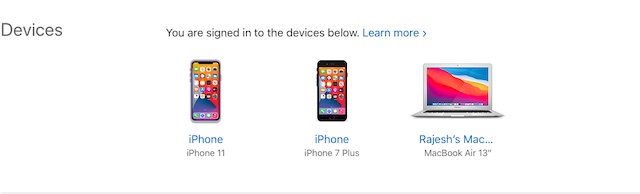
Open a web browser and head over to appleid.apple.com. Then, sign in to your account and tap/click on a specific device and remove it if you no longer want it to be associated with your Apple ID.
If you feel concerned about the security of your Apple ID, I would recommend you to enable two-factor authentication. When 2FA is turned, your account gets an additional layer of safeguard that asks for verification every time anyone tries to sign in to the account. To further enhance the safety of your account, 2FA sends the verification code only on the trusted device.
To turn it on, head over to Settings app -> Profile -> Password & Security -> Two-Factor Authentication. Now follow the instructions to enable it.
Check If There is an Unexpected Alternate Face/Touch ID Set-Up on Your Device
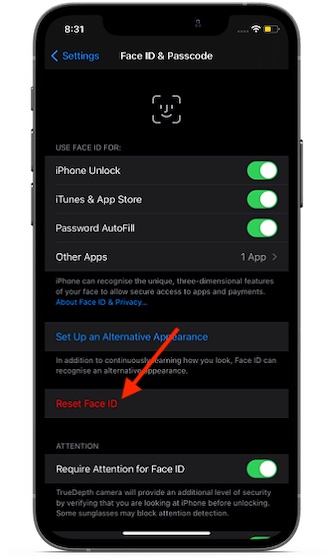
Another security setting that you must check is the alternate Face or Touch ID setup. Maybe someone got access to your iPhone and set up the facial/fingerprint unlock to access your device and pry into your private photos and notes. Head over to Settings app -> Face/Touch ID. If there is an alternate facial unlock or fingerprint setup, remove it.
Review All the Installed Apps and Delete the Ones You Don’t Recognize
From a security perspective, it’s always better to keep a track of all the apps that have been installed on your iPhone. Knowing the fact that custom apps can be manipulated to access sensitive data, you should always guard against them, making sure they do not exist on your iOS device.
Thanks to App Library, it has become pretty easy to access specific apps on the device. All the apps are organized in different categories like entertainment, games, and productivity so that you can find a specific type of app with ease. What’s more, you can also view them in the list view by simply tapping on the search bar to scroll through all the installed apps. Note:
It’s no secret that outdated apps are vulnerable to hacking and even tend to create plenty of problems like draining the battery and slowing down the device. Therefore, you should keep apps updated. iOS lets you update apps both manually and automatically. You can head over to App Store -> Profile and then update all the apps at once. If you wish to update apps automatically, navigate to Settings app -> App Store. Under the Automatic Downloads section, turn on the switch for App Updates.
Delete Unknown Configuration Profiles
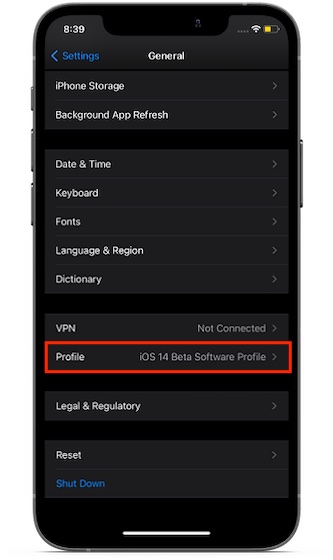
Companies and educational institutions use mobile device management tools and device profiles to manage devices and even access data. Though no one can argue the usability of MDM and device profiles, there have been numerous instances where they have been used to access data and location information on the device. Therefore, you need to ensure that there are no unknown configuration profiles installed on your iPhone or iPad. To delete a profile or MDM configuration from your iPhone, iPad, or iPod touch: Navigate to Settings app -> General -> Profiles & Device Management. Now, select the profile and hit Delete Profile. After that, restart your device.
To remove a profile from your Mac: Head over to System Preferences and click on Profiles. Next, click the suspicious profile and then click on the Remove button (-) below the list of profiles. After that, click on Remove again to confirm the deletion. After that, restart your Mac (click on the Apple menu and choose Restart).
More Tips to Secure Your iPhone and iPad from Unauthorized Access
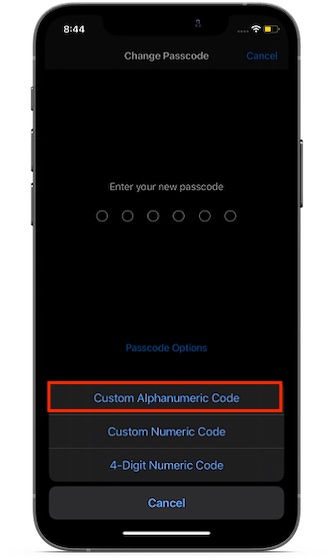
iOS offers several ways to secure your iOS device from unauthorized access. There are three notable security features that I would want you to take note of. Set up alphanumeric passcode: Head over to Settings app -> Face/Touch ID -> Change Passcode -> Passcode Options -> Custom Alphanumeric Passcode.
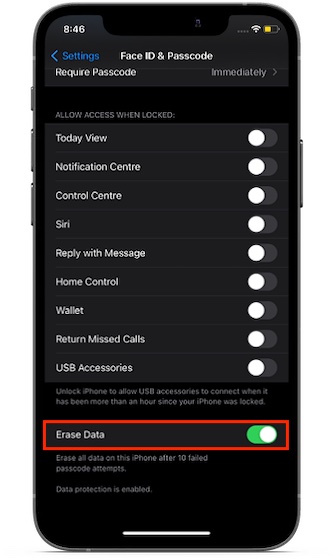
Automatically erase your iPhone after 10 failed passcode attempts: Settings app -> Face/Touch ID -> Erase Data.
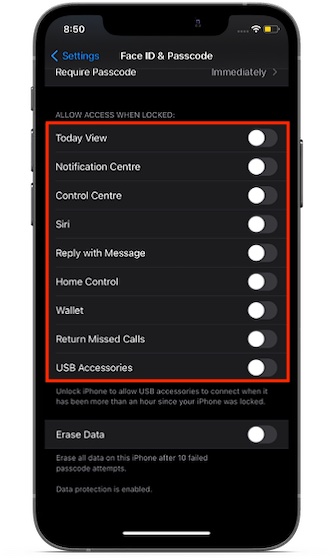
Secure Lockscreen: Settings app -> Face/Touch ID. Under Allow Access When Locked section, turn off the toggles right next to today view, notification center, control center, Siri, Replay with Message, Home Control, Wallet, Return Missed Calls to secure the lock screen of your iPhone.
Moreover, there is also an option to force the iPhone to ask for a passcode to allow USB accessories to connect when it has been more than an hour since your iPhone was locked.
Take Control of Your Device Access to Ward off Foul Play
There you go! So, that’s how you can bolster the security of your iDevice to block unauthorized access. It’s just about checking off the basics and making sure all the security measures designed are active. Now that you know how to shield your device, make the most of the tips to keep your private information safe. You may also like to read these privacy-related iOS 14 articles:
Limit Third-Party Access to Photos App in iOS 14 and iPadOS 14 How to Manage Local Network Access of Apps in iOS 14 Enable Private MAC Address on iPhone in iOS 14 How to Stop Apps from Accessing Your Precise Location in iOS 14 How to Manage Location Data Access for Widgets on iPhone and iPad
By the way, do you have any question or feedback? Be sure to shoot it in the comments below.